Two nights ago, Wikileaks started releasing what the whistleblowing platform dubbed as the #Vault7 Series of damaging information into the inner workings of the CIA.
The first iteration “Year 0” describes the specific tools that the Deep State agency has been using against its friends and foes.
Said tools include ways and means to penetrate and control the firmware of your smartphone, smart TV, laptops, desktop computers, and your smart car.

In fact, any piece of electronic equipment, which has a basic programmable CMOS chip in it, can be manipulated to work according to their whim, for as long as the battery is in place.
Dumb Chips in Smart Appliances
A CMOS chip is composed of several electronic switches which can be used to store instructions and data, when coupled to a power source. Billions of these electronic switches in one chip make a CPU, i.e. the brain inside your laptop.
A firmware is a cross between a software and a hardware. While a software contains instructions for the hardware to comply, a firmware is instruction and hardware in one.
The CMOS is the hardware, and instructions are electrically written, or programmed, into it making the whole assembly as the firmware. It is the first to act when a computer, or any smart devices, are turned on, subsequently performing the necessary bootstrap preparations, self-checking routines, and loading of the operating system, afterwhich the apps could then run.
Without the instruction starting at the firmware, any hardware or gadget is just a piece of junk.
Laptops, personal computers, and similar devices are all using CMOS firmware that are usually connected to a coin battery, so that even if it looks like the appliance is switched off, it is not.
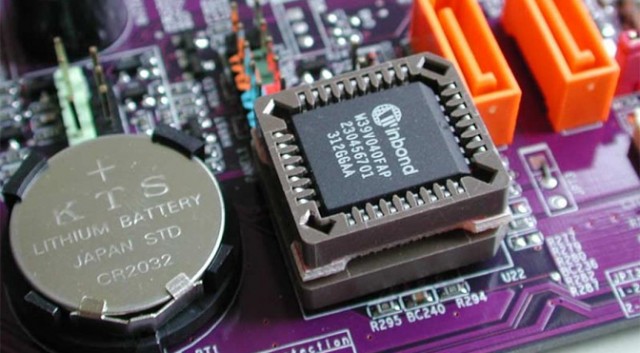
CMOS in smart appliances is far more advanced which may also employ supercapacitors, which can store large amounts of energy.
Solid state storage disks used in your laptop, for example, are not only made up of thousands of CMOS chips, but is also utilizing supercapacitors as its own source of power to maintain data. In short, the embedded power source may not, at all times, look like a battery, and the appliance need not be connected to any convenience outlet.
Even our smartphone’s camera sensor is also made up of CMOS chip…
To put it bluntly, all Smart TVs, not just Samsung brand, and all smartphones, can be used to monitor our living rooms, everywhere we go, and in real time.
And no matter how application developers implement their encryption, the CIA would just bypass it, as Vault7 Year 0 reveals.
CIA malware and hacking tools are built by EDG (Engineering Development Group), a software development group within CCI (Center for Cyber Intelligence), a department belonging to the CIA’s DDI (Directorate for Digital Innovation). The DDI is one of the five major directorates of the CIA (see this organizational chart of the CIA for more details).
… The CIA’s Mobile Devices Branch (MDB) developed numerous attacks to remotely hack and control popular smart phones. Infected phones can be instructed to send the CIA the user’s geolocation, audio and text communications as well as covertly activate the phone’s camera and microphone.
These techniques permit the CIA to bypass the encryption of WhatsApp, Signal, Telegram, Wiebo, Confide and Cloackman by hacking the “smart” phones that they run on and collecting audio and message traffic before encryption is applied.
- https://geopolitics.co/2017/03/07/cia-malware-targets-iphone-android-smart-tvs-vault7-year0/
It’s the least of our concerns?
Just look at how social media trolls are using smartphone cam videos to blackmail students and housewives, for extortion and sex slavery purposes. These trolls are just amateurs, they got caught by the authorities eventually.
Imagine if the authorities themselves, the CIA, or the FBI, has all the tools in their arsenal to do all of these things far more efficiently, and in the name of “national security.”
What could possibly go wrong?
CIA Surveillance & Assassination
Nowadays, data and programming instructions can be sent through a variety of channels, i.e. internet, power lines, and wireless.
Power-line communication (PLC) is a communication method that uses electrical wiring to simultaneously carry both data, and alternating current (AC) electric power transmission or electric power distribution. It is also known as power-line carrier, power-line digital subscriber line (PDSL), mains communication, power-line telecommunications, or power-line networking (PLN).
- https://en.wikipedia.org/wiki/Power-line_communication
The ability to send programming signals wirelessly, and through the household and distribution power lines, puts everyone in danger of being under surveillance and assassination even when not connected directly to the internet.
Surface mounted components inside smartphones look all the same. The best way to shut them off is to tear them apart, or cook them in an oven.

The only safe cars are those without any piece of electronic “enhancements,” e.g. programmable electronic fuel control [EFC], electronic brakeforce distribution [EBD], and electronic gear-shifting system. Otherwise, a quick increase on the voltage supply to your EFC would simulate a hard press at the accelerator, while a sustained low voltage signal on your brake system may disable it for good. Not a good combination along superhighways.
Imagine what the full implementation of the driverless cars could accomplish.
If you own a plane, they can hack it, too. Of course, we have known how the Malaysian Boeing jumbo jet just dropped out of its flight path and never to be seen again.
In short, the Deep State can monitor your activity 24/7 without you even realizing it, and when needed, plunge your car into a deep ravine on your way home.

They have this capability, not in some distant future, and certainly not in some fiction movies, but right here and now.
Imagine what could be leveraged from the full digitization of your wallets, and the full microchipping of the population entails.
Imagine what wifi hacking vis a vis Transhumanism could achieve.
Analysis
The first #Vault7 release, “Year Zero,” is less than 1% of the entire #Vault7 data dump. Whatever the contents of the remaining 99% must be more devastating than the first.
We can only speculate that the next Vault7 iteration will be more about their specific targets and victims since the day they’ve obtained these tools, in much greater detail than the Edward Snowden NSA surveillance leaks have revealed.
Having the appetite and ability to:
- launch a 24/7 surveillance on any targeted individual, blackmail and assassinate the same when necessary, and;
- launch color revolutions against independent governments, and supposed allies;
- launch color revolution even within the United States itself, as it is now doing against a legitimate Trump government, and;
- dictate specific targets for Pentagon armed operation/invasion, or through private mercenary groups around the world;
… the Central Intelligence Agency has proven itself to be the most dangerous intelligence organization within the Deep state infrastructure.
Both NSA and the CIA are rivals when it comes to unregulated snooping, and the Trump administration intended to destroy the latter by using the former. Sadly, Mike Flynn went to the exit door prematurely.
Nevertheless, Trump’s offensive accusation about Obama’s wiretapping, and the subsequent Wikileaks #Vault7 confirmation of the CIA’s ability to leave Russian hacking footprints in all its snooping activities, are putting the Deep State in an uncomfortable defensive “will investigate further” mode.
We also suspect that more sordid details about the PedoGate and PizzaGate scandals will also come to the fore. Surely, there will be more than enough evidence to bring the Khazarian Mafia puppets in DC, and in Brussels, to justice. But will the people of the West ever demand so?
Interestingly, even the Pope has gone on PR hyperdrive by appearing on the Rolling Stone magazine, you know, to get the people distracted.
#PopeFrancis was a #RollingStone: #Pontiff to star on cover of iconic rock mag https://t.co/CJjmk9VAlw pic.twitter.com/V7BSlJuwuT
— RT (@RT_com) March 9, 2017
Lo and behold, they’ve even resurrected the butcher of Iraq!
https://twitter.com/IntheNow_tweet/status/839925111599869952
Aside from the Deep State/CIA’s surveillance and assassination capabilities, we can also extrapolate that they can control the entire interconnected fiat financial system of the planet, through the use of these hacking tools, in conjunction with banking personnel blackmail. We are already aware of the wrong “bankers’ suicide” some years ago.
Since the CIA is also massively involved in pharmaceuticals and bioweaponry, we can anticipate that the deeper truths about autism, AIDS and cancer, will see the light of day.
Not that we have no information about them already, but a confirmation of their lies will be much appreciated, as all of these revelations, from Bradley Manning to Ed Snowden, and all those files that the Wikileaks whistle-blowing platform has published so far, validated all of the “conspiracy theories” in the 60s and beyond.
Most significantly, all of the above discussions prove that the real tinfoil asshats are those people working in the mainstream media, while the Deep State CIA is also stabbing Khazarian Mafia’s best friends on the back.
https://www.youtube.com/watch?v=EQsLB7iyUMI
Conclusions
The “internet of things,” or IoT, is a very potent tool for mass surveillance and assassination. It’s either we go off the grid, or we get rid of agencies like the CIA & Co. because wherever the CIA goes, MOSSAD and the Vatican Intelligence are not too far behind.
Already, the Deep State mainstream media are moving heaven and hell to contain the Wikileaks Vault7 “Year 0” CIA dump fallout. If they were struggling with Trump’s “Obama snooping during the campaign” accusations, how much more with the full uncloaking of the Deep State’s primary weapon of mass destruction?
Their continued focus on non-issues [except in CIA-controlled regimes] such as transgender and women’s rights, or the “epic Barcelona comeback,” or Bieber’s “fake 900 child sex offense charges,” all reflect about their advancing irrelevance.

Their only remaining overused counteroffensive narrative is:
The Russians did it, again.
The mainstream media’s pathetically double standard is more than glaring.
https://www.youtube.com/watch?v=oF6GroMUtaE
Will the Wikileaks organization be able to “break the CIA into pieces and scatter them into the wind,” as its password to the “Year 0” Vault7 iteration suggests?
SplinterItIntoAThousandPiecesAndScatterItIntoTheWinds
… a befitting honor to John F. Kennedy’s wishes before his assassination.
“I will splinter the CIA into a thousand pieces and scatter it into the wind,” were his exact words, according to a Kennedy administration official who spoke with The New York Times for a report published three years after JFK’s death.
In order to answer the question, we must consider two contrasting viewpoints. The move towards the full establishment of a Technocratic Dictatorship in the West is still in full swing.
Evidence like the massive move to a cashless society in Europe is still ongoing, and even in the BRICS member India, under the able assistance of Bill Gates Foundation [here], although in other instances, the Modi government is banning Gates’ vaccination efforts [here].
The other viewpoint is that a move like this one from Wikileaks, and the ongoing Russian-led military intervention in Syria, are decapitating the Khazarian Mafia’s systematic encroachment to the few countries still left unconquered. Add to that is the growing independence of the ASEAN community from the diktats of the West.
If the Western population could implement the best in science and technology, while completely removing the Oligarchy from the whole picture, or they could take away the “dictators” from Technocracy, as the Wikileaks’ Vault7 Series necessitates, then we can say that the Khazarian Mafia cum Deep State will become history. But that is a big if.
One thing is sure though: the agency may be the deadliest of its kind because of its willingness to pull the trigger, but not necessarily the smartest one as the massive Vault7 leak is suggesting.
To top it off, knowing that they’ve been monitoring our conversation online, we can also turn these aggressive offensives into some golden opportunities by telling them exactly what we think of them, or just about anything that our heart desires,
Now this is funny #Vault7 #CiA pic.twitter.com/UOURLGiY9x
— Local Business Cons (@localbusinessco) March 8, 2017
… knowing fully well that they are engaged in real-time violation of our constitutional rights, and have committed treason of the highest order against the Republic.



PROMIS, was developed and sold by INSLAW. The program was stolen by the DOJ, MOSSAD, NSA, and CIA about 1980. Further developed by Judaism´s MOSSAD and the CIA, PROMIS was sold around the world by the CIA for a profit of 40 million dollars, by 1992.
PROMIS was no doubt the source of the secretive programs that the CIA has further developed to use within programmable I.C.s that are always powered by a coin battery. Electrical devces that remain plugged in although turned OFF are subject to additional spy techniques. Per former MOSSAD agents, Judaism´s MOSSAD and the U.S. CIA have used PROMIS to spy on nations and agencies within nations, around the earch since 1982.
The budgets of the CIA, NSA and FBI should be trimmed so as to support only the functions that are described in their charters.
I wrote a brief expose” about three years ago-before Snowden came forward about the fact there is no privacy at all anywhere. This report gives lots of details on how it is done. We need hard line methods on how to search for and eliminate all the bug systems in quick and easy ways. Something like how the detective early method of non detection was to jump into the shadows or dart behind a wall. That sort of thing. All of society may become un-civilized otherwise. This was a great article. Thank you. Dr.Ronald Cutburth, engineering scientist, intelligence expert.
wrong again brisk breath it’s mossad aka cia
It is the duty of every peace and justice loving person on this planet to completely and utterly destroy all these so called intelligence agencies off face of our beautiful planet. Murder and mayhem to further the agenda of a select few has to stop